22 October, 2025

DevOps is a set of practices that enable the integration of software development, testing, and operations into a single holistic process. Traditionally, the integration of these processes happened at the end of the software development lifecycle and this approach is no longer considered efficient. The DevOps or the continuous integration and continuous delivery (CI/CD) approach, provides several benefits like quicker software delivery, increased collaboration, and higher quality.
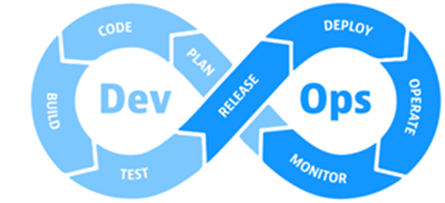
Figure 1 – DevOps Process
But with this shift toward speed and automation, critical questions arise:
This is where DevSecOps—the integration of security into every phase of DevOps—comes in. The goal is not to trade agility for safety, but to weave both together. From a GRC perspective, success depends on embedding security into both culture and processes without compromising velocity or innovation.
Let’s discuss how DevSecOps (Security-integrated DevOps) can be implemented and delivered without impacting the agility of the overall approach.
At the core of DevOps implementation, there is heavy reliance on automation for running tests, checks, deployments, etc., to build a seamless CI/CD pipeline requiring minimal manual intervention.
Integrating security in each of these areas requires a similar automation without impacting the flow or the timelines. At the same time, there should be no compromise on the security posture due to these additional requirements.
For some, this can sound like a complicated task that they would prefer to avoid, however, careful consideration toward automating most of the traditional security efforts, without impacting the core goals of the DevOps, will act as an enabler toward enhanced security.
From an executive perspective, there are two initiatives that can allow security to be adapted across DevOps and make a significant impact. These initiatives include embedding security into both culture and processes, supported by the right technologies.
The change in the mindset around the concept of security is everyone’s responsibility. This needs to be established and implemented. To do that, it goes without saying that security should be involved from the early stages of software design, and it always feeds back to the development process as it evolves.
![]()
Figure 2 – Security involved from early stages of software design
Key areas like application security, infrastructure security, CI/CD pipeline, and security monitoring need to be realigned according to the core requirements of the DevOps process. Establishing appropriate processes and introducing the relevant technologies is critical to accomplishing security goals without compromising the speedy delivery of software promised by this approach.
According to Verified Market Research, the global DevSecOps market was valued at US$9.72 billion in 2024 and is projected to reach US$22.71 billion by 2032, growing at a CAGR of 12.98% from 2026 to 2032. This clearly shows the overwhelming reception and push from the industry regarding the adoption of the DevSecOps process. While this trend provides significant benefits, it should not come at the cost of reduced security.
Despite any actions taken to enhance the processes and overall security focus, the end result should always be independently tested. Usually, teams tend to “mark their own work” given all the effort put forward to deliver whatever they have been tasked to do. It is of high importance to account for the necessary time to verify the end-solution as a whole.
Learn more about CPX’s Cyber Consulting Services.
Organizations can reach out to cyber risk management consultants to review, discuss, optimize and further enhance their DevOps approach/lifecycle.