29 October, 2025

APIs have evolved, and so have the attacks targeting them.
GraphQL, the modern query language designed for efficiency and flexibility, is rapidly replacing REST across industries. But with that flexibility comes a hidden cost: security blind spots that many organizations overlook.
Unlike traditional REST APIs with fixed endpoints, GraphQL gives clients the freedom to query exactly what they need, and attackers, the freedom to ask for a lot more. From introspection leaks and injection attacks to denial-of-service (DoS) via complex queries, GraphQL’s design can quickly turn from powerful to perilous if left unchecked.
In this blog, you will learn:
Because when it comes to GraphQL, what you don’t lock down could be what brings your system down.
GraphQL vulnerabilities generally arise due to implementation and design flaws. Unlike REST APIs that expose fixed endpoints, GraphQL allows clients to query exactly what they need in a single request.
GraphQL’s dynamic querying model:
These features increase developer productivity—but they also give attackers a lot to work with.
Why it matters: GraphQL is powerful and flexible, but that flexibility can be a double-edged sword. While it helps avoid common REST issues like over-fetching, it also introduces new attack vectors that aren't fully addressed by the OWASP API Top 10.
GraphQL is a query language for APIs, developed by Facebook and open-sourced in 2015. Unlike REST, it enables you to request only the data you need, in the structure you desire.
A GraphQL endpoint is usually a single HTTP endpoint (e.g., /graphql) that accepts POST or GET requests. It’s impractical to list all permutations of endpoints associated with a GraphQL instance. However, many GraphQL APIs, especially those built with frameworks like Apollo, commonly use standard endpoint paths such as:
/v1/explorer
/v1/graphiql
/graph
/graphql
/graphql/console/
/graphql.php
/graphiql
/graphiql.php
(...) A comprehensive list can be found on https://github.com/danielmiessler/SecLists/blob/master/Discovery/Web-Content/graphql.txt.
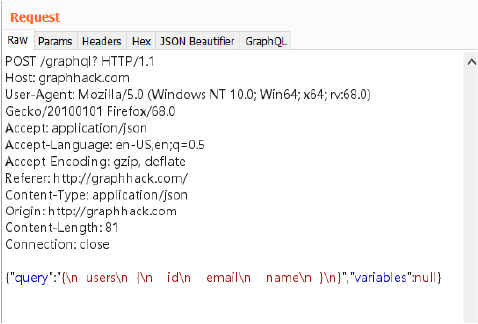
Sample GraphQL Request
Another effective method to identify hidden GraphQL endpoints involves searching JavaScript files for keywords like "query", "mutation", or "graphql". This can reveal unofficial or decommissioned GraphQL endpoints.
1. Information disclosure
GraphQL’s introspection feature allows clients to query the schema, which is useful for development but risky in production.
2. Injection attacks (SQL, NoSQL, Logging)
GraphQL queries are structured, but the parameters they carry can still be used for injection attacks—especially SQL injections—if resolvers pass user input directly to a database.
3. Denial of Service (DoS) via complex queries
GraphQL allows nested queries, which can lead to denial-of-service (DoS) attacks through overly complex or deeply nested queries.
4. Authorization bypass
Unlike REST, where authorization can be applied per endpoint, GraphQL operates on a single endpoint. This requires fine-grained, field-level authorization, which is often overlooked. GraphQL doesn’t enforce authorization by default.
5. Insecure defaults in popular libraries
Many GraphQL server implementations ship with insecure default configurations that can expose applications to serious risks if left unchanged (e.g., Apollo Server’s tracing and debug modes).
6. GraphQL CSRF
GraphQL can be used as a vector for CSRF attacks, whereby an attacker creates an exploit that causes a victim's browser to send a malicious query as the victim user. Let’s understand this more with an Exploit POC:
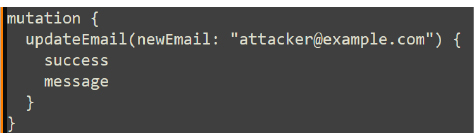
Scenario: Updating a user’s email via CSRF
Assume the GraphQL mutation looks like this:
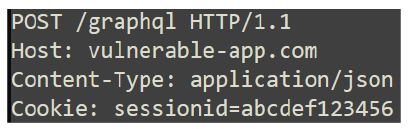
And it’s accessible via a POST request to:
It is assumed that,

Malicious HTML POC
If the server strictly enforces application/json, CSRF via browser is harder. But we can bypass this with a Custom Request (Using JavaScript + JSON) but only if CORS misconfiguration allows application/json cross-origin requests

Bypass with a custom request
Mitigations
7. Alias overloading
Here the attackers overload a query with many aliases for the same field, causing the backend resolver to execute that field repeatedly. This can overwhelm server resources, leading to a Denial of Service (DoS), amplify the impact of a query, or extract more data than intended.
This can be Defended with query cost analysis & alias limits - block queries with repetitive fields under different aliases to prevent data extraction/DoS.
While OWASP API Top 10 covers high-level risks (like Broken Object Level Authorization and Excessive Data Exposure), GraphQL introduces new layers that require additional scrutiny:
| OWASP Category | GraphQL Amplification |
| API1:2019 - BOLA | Needs per-field authorization checks |
| API3:2019 - Excessive Data Exposure | Exposed through flexible querying |
| API4:2019 - Lack of Resources & Rate Limiting | Exploited via deep/complex queries |
| API7:2019 - Security Misconfiguration | Introspection and default settings |
Testing tools significantly simplify GraphQL testing by visualising schemas and automating common tasks. Below are particularly useful tools for pentesting GraphQL vulnerabilities more efficiently:
When deploying GraphQL at scale, organizations must move beyond surface-level best practices and treat GraphQL as a core application surface that needs structured risk management. Here's how to do that effectively:
Deploy a GraphQL gateway like Apollo Router or Hasura with:
Run automated tests for:
Pro tip: Don't wait for a breach to harden your API.
Start with visibility: audit your schema, know what's exposed, and test like an attacker would. If you're not threat modeling your GraphQL surface, someone else probably is.
By proactively managing exposure, validating inputs, and enforcing strict authorization, by understanding these vulnerabilities and applying best practices, you can build robust and secure GraphQL APIs.
As the demand for faster, more flexible, and efficient APIs grows, GraphQL stands out as a transformative technology. GraphQL provides powerful tools for API design, but its flexibility also introduces new attack surfaces. Developers must adopt a security-first mindset and apply the same rigor to GraphQL that they would to any other API technology.
GraphQL isn't insecure by design—but it does require a different approach to API security. Its flexibility is both a feature and a vulnerability.
Looking ahead, the future of API development is increasingly client-driven, schema-first, and performance-focused—all of which align perfectly with GraphQL’s design philosophy. As usage grows, we need to treat GraphQL with the same attention we give to OWASP risks—if not more.
Ready to strengthen your GraphQL defenses? Get in touch to design secure, high-performance APIs built for the modern attack landscape.
References
https://cheatsheetseries.owasp.org/cheatsheets/GraphQL_Cheat_Sheet.html
https://www.yeswehack.com/learn-bug-bounty/hacking-graphql-endpoints
https://labs.detectify.com/crowdsource-community/graphql-abuse-bypass-account-level-permissions-through-parameter-smuggling/
https://github.com/m14r41/PentestingEverything/tree/main/API%20Pentesting/GraphQL
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/GraphQL%20Injection